IBM Beefs Up PowerSC GUI
Some early PowerSC commands have been wrapped into a GUI that makes once-opaque security and compliance tools more transparent and significantly easier to use.
Security and compliance management can be a challenge for AIX* users. It’s one of the reasons IBM introduced the PowerSC* solution. Until recently, however, using PowerSC required a strong understanding of the command-line interface to simply check if an organization was compliant with industry standards.
Some of those early PowerSC commands, beginning with PowerSC 1.1.5 and continuing with version 1.1.6, have since been wrapped into a graphical interface that makes once-opaque security and compliance tools much more transparent and significantly easier to use. And for good reason.
Safe and Compliant
Having greater control over security and industry regulation compliance can have a dramatic bottom-line impact, not only because of the high cost of a data breach itself, but also the fines that can be added to that if the affected company wasn’t in compliance at the time of the breach.
“It pays to remain compliant with industry standards such as PCI DSS and HIPAA,” explains Petra Bührer, offering manager for IBM Power Systems* Software. “The PowerSC GUI was designed with that in mind. In addition, it has very powerful features in terms of file-integrity monitoring—especially as we deeply integrate with the Power Systems Software stack and its security features, such as AIX Trusted Execution (TE)—to keep systems safe and compliant.”
To meet regulatory compliance, organizations are required to set system security up in a uniform manner to meet specific industry standards. Unfortunately, understanding and applying a particular standard can be a tedious, time-consuming and error-prone task.
Security Compliance Automation, a feature included with PowerSC, provides pre-built profiles that are certified to comply with industry standards such as PCI DSS, HIPAA, the Department of Defense Security Technical Implementation Guide for Unix (DOD STIG), the Control Objectives for Information and Related Technology (COBIT) and the North American Electric Reliability Corporation (NERC).
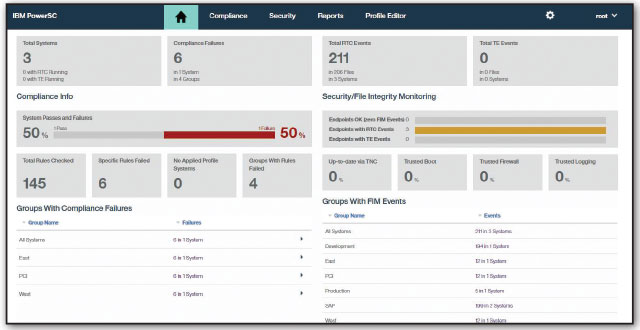
In the latest version, users can also monitor ongoing compliance in real time through the integration of File Integrity Monitoring (FIM) functionality. FIM recognizes changes in content or permission on important files and is a key piece of the compliance-enforcement picture. The security dashboard (see below; click to view larger) gives users a one-glance look at how well their servers are measuring up to compliance regulations.
“People are not only using PowerSC for the obvious purpose of making their systems more secure and compliant, but also to provide the required information through the provided report to prove they’re meeting compliance requirements. Security personnel have to be able to extract the information demanded by auditors, which is where PowerSC’s clear and concise reporting capabilities come into play,” remarks Tim Hill, senior product manager with Rocket Software, which co-developed the solution.
No One Left Behind
PowerSC 1.1.5 was primarily focused on compliance issues, which provided the highest value for most users. Version 1.1.6, which was developed based on client input, covers both compliance and security, while also offering reporting features. In addition, it integrates with other products such as IBM PowerVC* and AIX TE. For example, it provides improved malware intrusion prevention/detection capabilities thanks to centralized configuration and monitoring capabilities for FIM. If real-time compliance (RTC), which is a component of PowerSC, generates an event that indicates a user just modified an executable or permissions on a file, a notification is immediately pushed to the GUI and can automatically be emailed to the appropriate people. The same procedure applies for AIX TE events.
In order to provide an easy-to-consume report of overall system status, the PowerSC security and compliance dashboard provides a consolidated view of relevant AIX security tracking and protection components, offering a group-based view that users can employ to instantly spot which endpoints require the most urgent action. Additionally, security information can be integrated with higher-level tools such as IBM QRadar* Security Information and Event Management (SIEM), allowing relevant data to be viewed within other environments.
Multi-factor authentication (MFA), a new offering brought to the PowerSC family (PowerSC Multi-Factor Authentication 1.1.0) that will be released later this year, is a method by which system-access control is granted only after a user successfully presents several separate pieces of evidence, such as a password, a fingerprint and a cryptographic key, to an authentication service. If a hacker attempts to access a system, they will be shut out if one of the authentication methods fails.
The similar two-factor authentication (2FA) can also be deployed. Users submit two multifactors, typically a username and password and then a unique token. With both 2FA and MFA, users submit factors that are validated in one step instead of several. Because the factors are bundled together, a hacker trying to gain access to a system would have no idea which of the authentication factors failed, making it much more difficult for the hacker to gain access.
On the other hand, multi-step authentication (MSA)—where authentication factors are broken up into individual components, such as username followed by password—has the potential for data leakage, where a hacker can determine which steps of the authentication failed. With MFA and 2FA, the hacker won’t know where the authentication failed.
Understanding the differences between MFA and MSA is critical, because MFA will become a PCI requirement as of Feb. 1, 2018. In fact, PCI 3.2 Section 8.3 requires MFA for any personnel with administrative access to environments handling credit card data, whereas previously it was used only for remote access from untrusted networks.
“If clients don’t have that, they’ll become noncompliant and will have to take credit card data off their AIX systems. That’s why we’ve been so focused on coming up with this new offering,” Bührer remarks. “We don’t want to leave anyone behind, which is also why we’ve made this available as a standalone offering, without any PowerSC Standard Edition dependencies.”
One of the key strengths of PowerSC is its deep integration with the entire Power Systems Software stack, providing virtualization-aware enhancements built on top of IBM PowerVM* and integrating with PowerVC, IBM’s private-cloud management offering based on OpenStack. This means that PowerSC capabilities can be spread across an enterprises’ entire AIX OS-related service environment. (Clients should expect Linux* support within the next year, and the team supporting it is currently working with some clients to determine the most critical aspects to include.)
A Centralized Interface
In essence, PowerSC is intended to simplify many functions in terms of promoting security and compliance through automation, parallel operations, compliance templates, real-time alerts and auditing reports. This helps reduce the complexity involved in becoming and remaining compliant and keeping your environment secure—no command-line expertise needed.