PowerSC as an Endpoint Detection and Response Solution
Ahmed Mashhour, an IBM Power Systems Global expert, explains the value of using PowerSC for end point detection and response (EDR)

A critical point of security in any IT environment is the endpoint, and that’s where endpoint detection and response (EDR) comes in. As suggested in the name, EDR focuses on identifying and addressing security threats at the endpoint level, be it clients, machines or other entities. EDR solutions continuously monitor endpoint activities and analyze data to detect potential threats in real time.
This may be easier said than done, but that doesn’t mean it has to be hard. For Power Systems, one easy solution for EDR implementation is PowerSC, an interface for managing your endpoints and ensuring full compliance.
A wide-ranging concept in the security world, EDR simply collects and analyzes data from endpoints, detecting suspicious behavior and then taking action. The suspicious behavior can be shaped as trojan programs, viruses and other malicious programs, data- and file-level integrity modification, critical data hash/signatures manipulation and endpoint network intrusion.
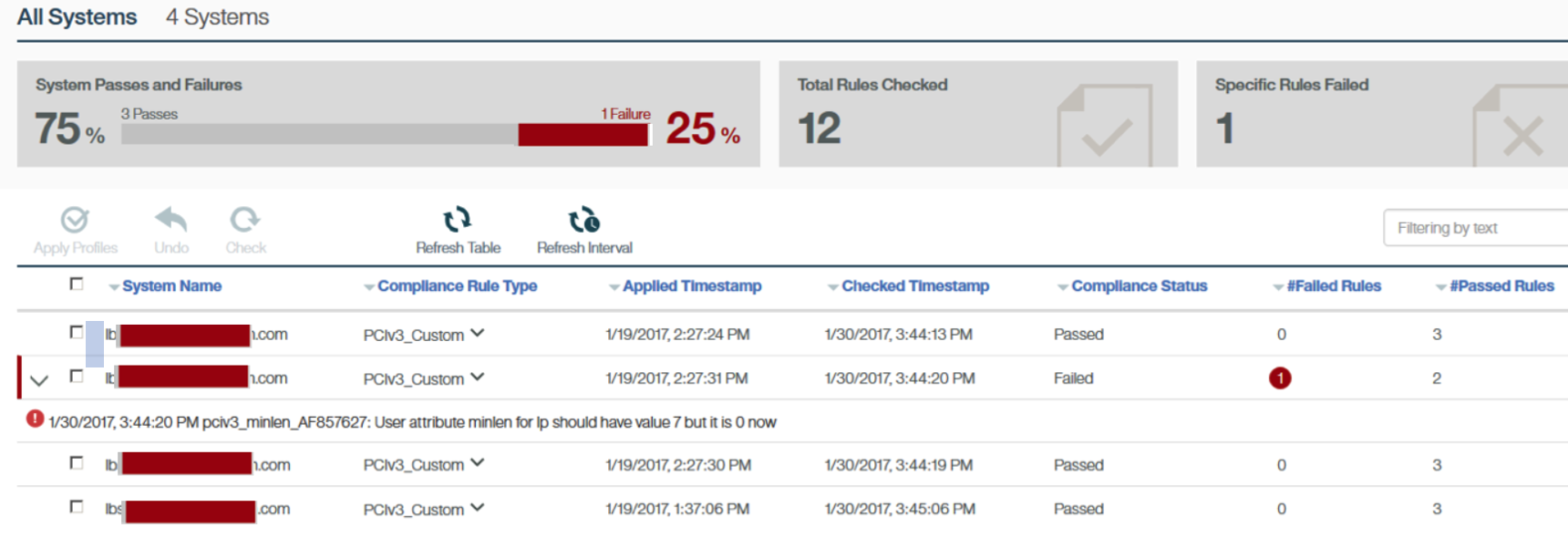
Significant PowerSC EDR Options
What makes PowerSC so powerful and easy is that the all the options you need are convenient to find, manage and customize with automated responses that are issued based on severity. Significant options include security compliance and automation, application files and libraries control, threat hunting, anti-malware mechanism and intrusion detection and prevention.
We’ll look at a few of these functions below.
Security Compliance Policies and Automation
You can change the default settings of AIX, VIOS, Linux, HMC or IBM i running on Power using PowerSC. This provides different types of security-hardening profiles in order to fulfill the specific type of security or regulatory requirements of your organization.
Application Files and Libraries Control
Application control can be achieved easily from the GUI interface against your different endpoints since the PowerSC understands the nature and the libraries of the endpoint operating systems.
This turns on the malware prevention mechanism in which you require executable files to be authorized before execution. An executable file not properly authorized would either be prohibited from execution or cause an error message, depending on the configuration.
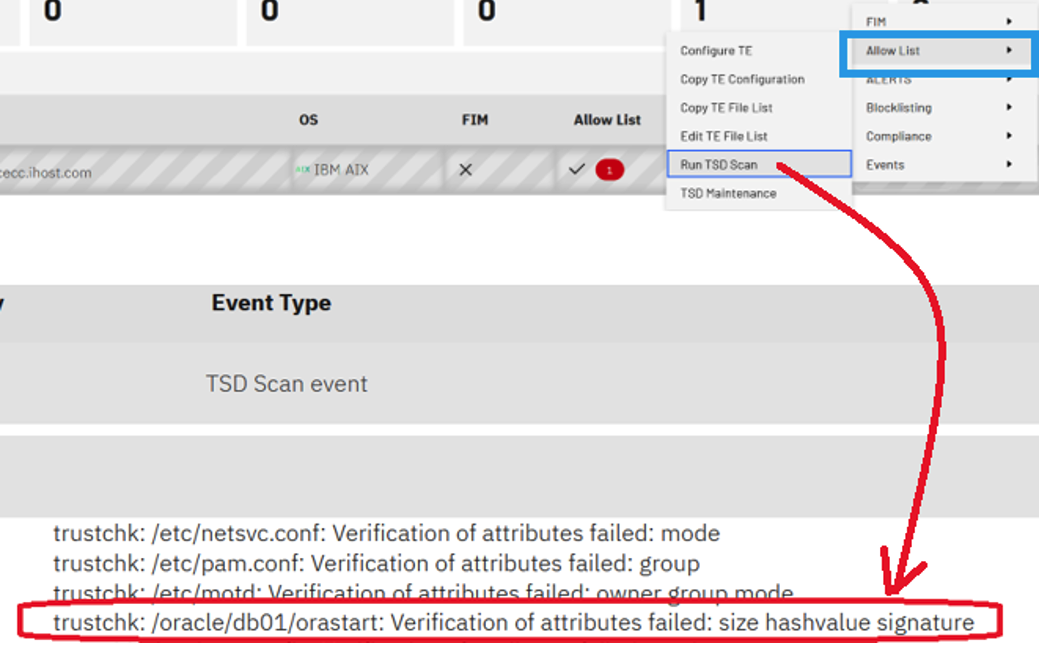
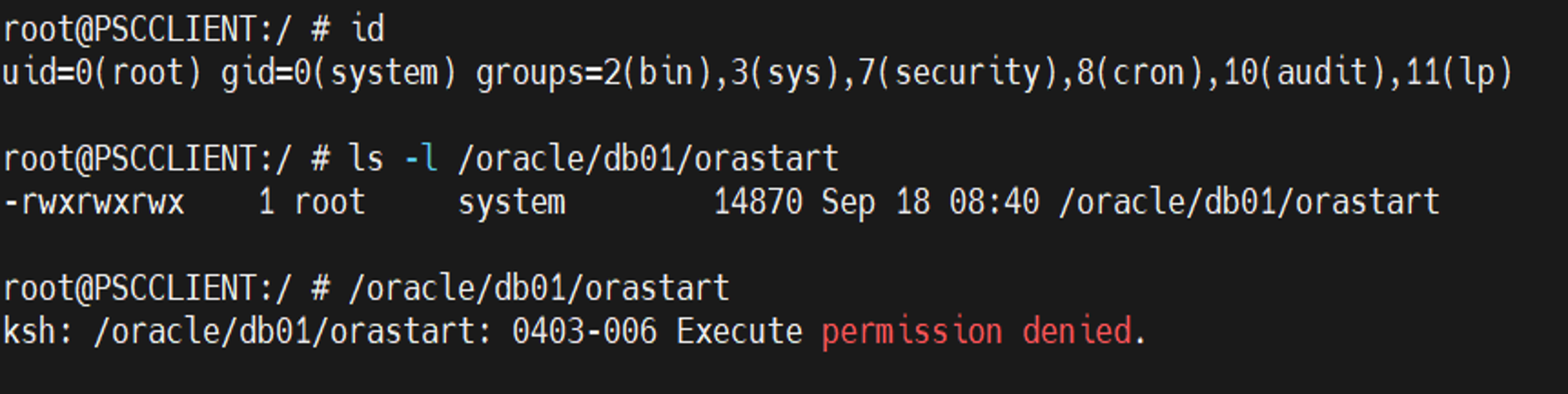
Threat Hunting
A threat hunting concept can be implemented through the block listing tab, where it scans files that match a list of user-provided virus hash values. When you periodically receive a list of new hashes and want to perform an on-demand or an automated scan of your endpoints, you can search for that set of hashes. It then reports it for the administrator to either take immediate action or configure an automatic action for future events.
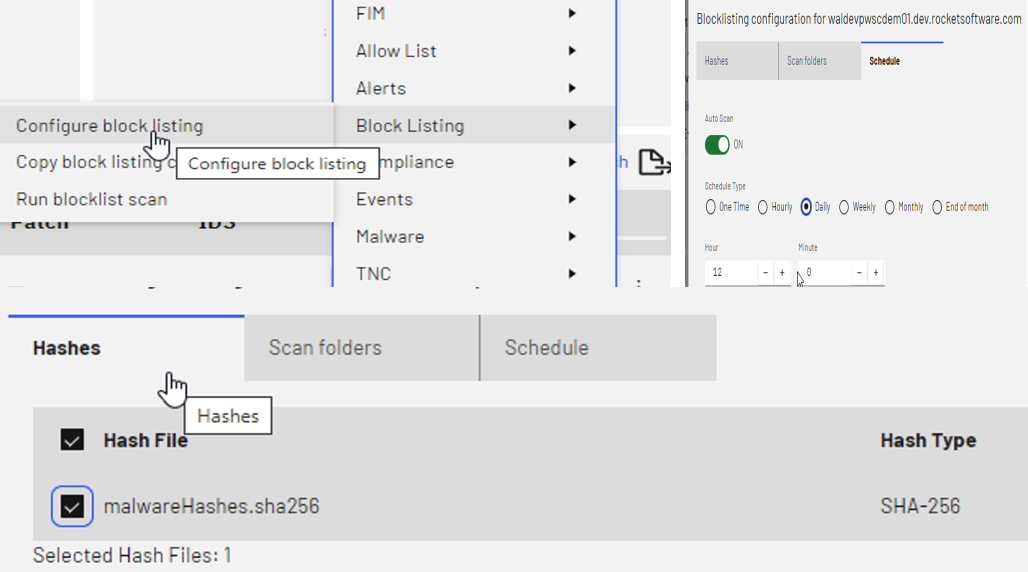
Anti-Malware Mechanism
The anti-malware capability in PowerSC addresses risks including ransomware and viruses. The PowerSC GUI server provides browser-based centralized management of the anti-malware against endpoints configured with the PowerSC GUI agent.
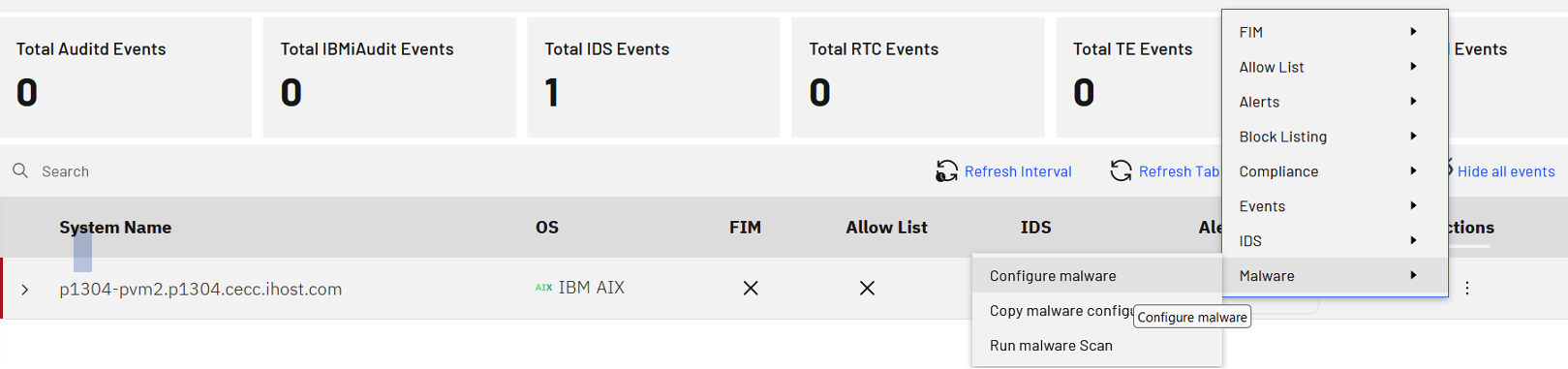
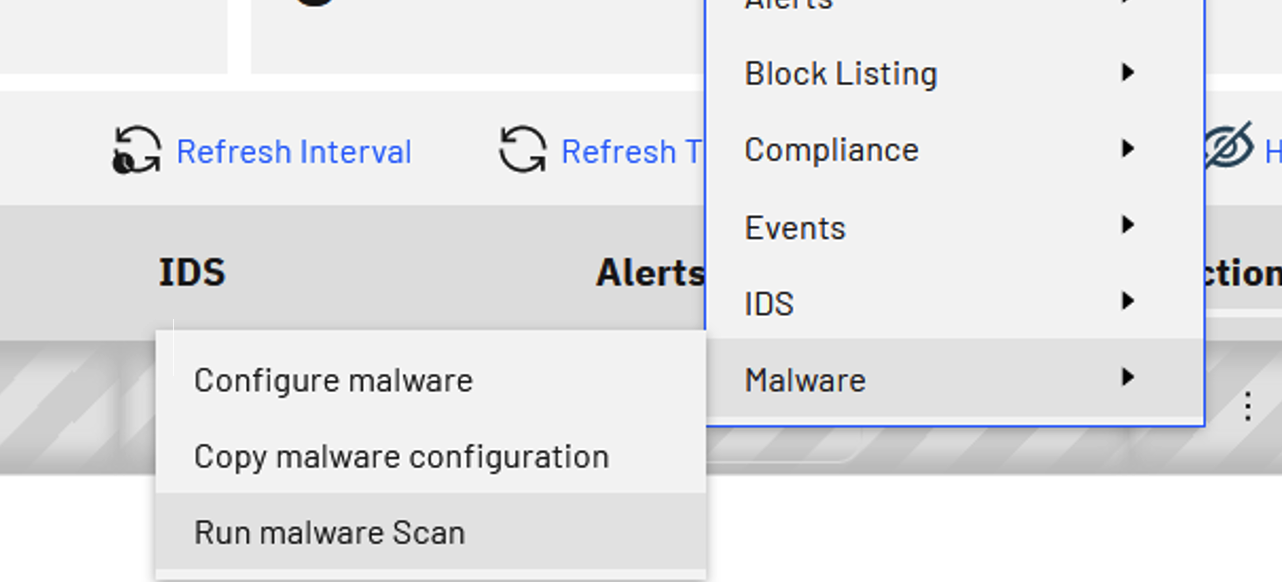
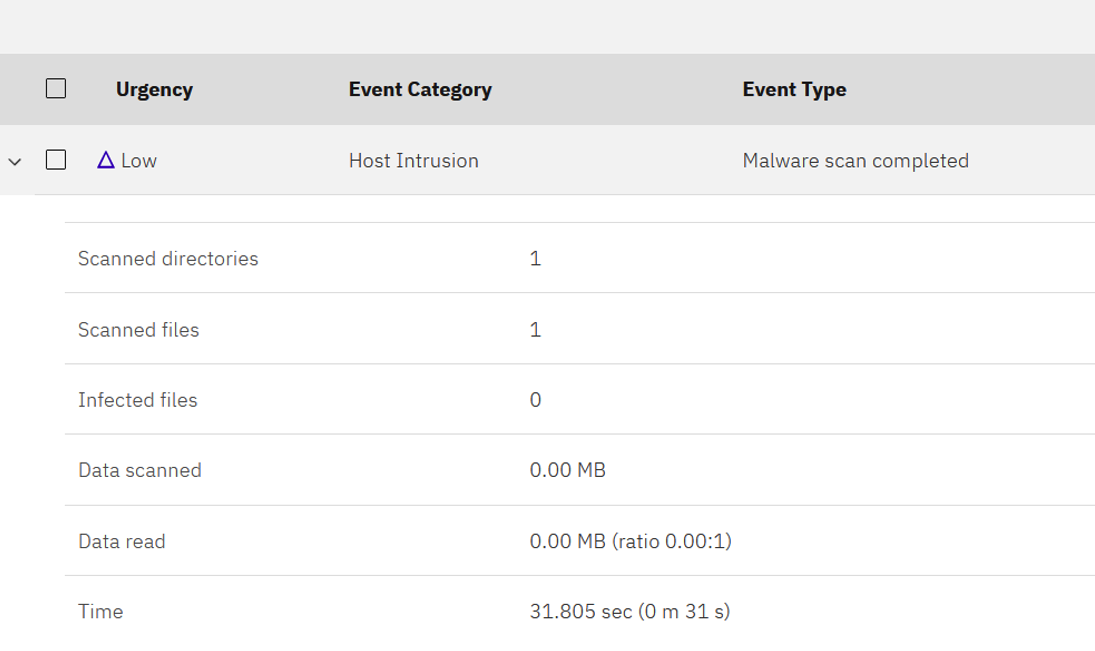
Intrusion Detection and Prevention
You can easily configure and manage the intrusion detection system (IDS) for a specific AIX, RHEL or SUSE Linux Enterprise Server endpoint. For AIX, the PowerSC centralized server allows you to use the IP security (IPSec) facility of AIX to define parameters for intrusion detection. In Linux systems, PowerSC allows you to use the port scan attach detector (PSAD) facility and make use of iptables log messages to detect, alert and optionally block port scans and other suspect traffic. A nice thing is that you can configure automatic responses/actions for such intrusion.
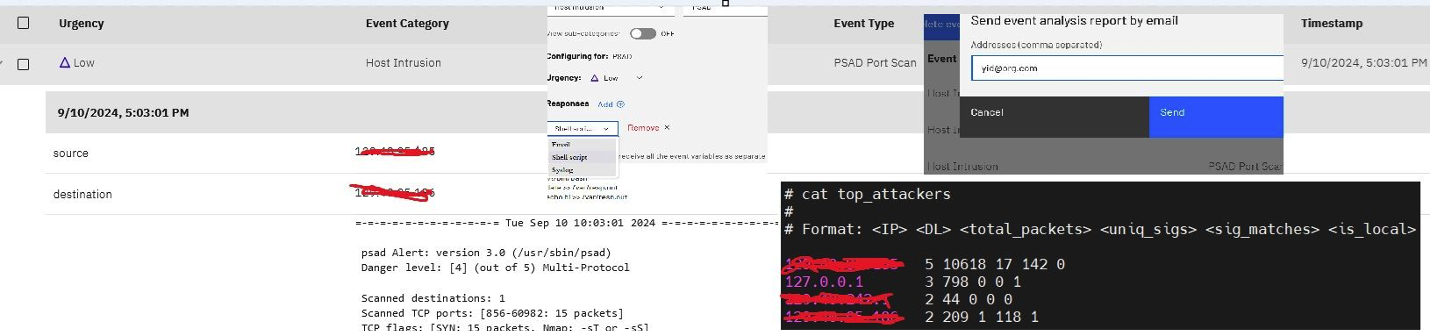
Figure 6: Checking and managing the intrusion aspects.
An Optimized EDR Solution
With its wealth of options for collecting data, analyzing data, detecting problematic phenomena and taking action, PowerSC provides a robust and user-friendly EDR solution for IBM Power environments. Because it is optimized for these systems, PowerSC is is able to offer the automation and degree of control that security professionals are looking for.