IBM Tools Support Layered Data Privacy and Protection
Data today is on the move. It’s traveling from the server to the storage area network, from the enterprise into the cloud, or even to third parties. Although the IBM Z® platform protects data on the platform with pervasive encryption, the data can be vulnerable the moment it leaves the mainframe. Data can be breached by side-channel attacks in the public cloud, by poor security practices on third-party platforms, by spoofing attacks designed to intercept traffic intended for an approved storage network, and even by employees. As if these issues weren’t challenging enough, companies need to also contend with a rapidly proliferating array of data-privacy regulations. And in the meantime, they need to deliver the products and services their customers expect.
What’s a data administrator to do?
Start with strategy. The protection needs to be layered. IBM supports that layered approach with a pair of new offerings for IBM z15™: IBM Data Privacy Passports and IBM Fibre Channel Endpoint Security. Data Privacy Passports creates trusted data objects, while Fibre Channel Endpoint Security ensures trusted storage endpoints. In combination with pervasive encryption on the platform and IBM tools for trusted execution, the z15 is designed to provide the layers of protection necessary to enable organizations to combat security breaches.
Data Privacy Passports provides a centralized means for protecting eligible data everywhere it exists: on the system of record, in the cloud, in flight and outside the organization. This protection holds whether the data is in the hands of legitimate business partners or hackers, as any access to the data requires a trip back to Data Privacy Passports. Fibre Channel Endpoint Security authenticates the storage device and guarantees a secure, encrypted connection for all traffic flowing on a link between host and storage controller. Just as important, the offerings provide tools for maintaining compliance with data privacy regulations, as defined by established policy.
Trusted Data
The reality of moving data out into the world can be sobering. A survey of over 1,000 IT organizations in the US and UK revealed that 59% had experienced a data breach originating with a third party (bwnews.pr/2Wr76S7). Yet sharing data with outside organizations is increasingly a part of the business landscape, whether as a choice, such as traditional financial services organizations partnering with fintechs, or as required by legislation. In the EU, for example, banks are compelled to satisfy requests for customer data stemming from mobile pay services, but they have no way of knowing whether those third parties have effective protection in place. Data Privacy Passports provides provide a method for companies to ensure the security and privacy of sensitive data no matter where it’s located.
The offering was built with three general objectives:
- Protection through encryption everywhere combined with the ability to revoke access
- Data privacy compliance through consent and centralized privacy controls
- Proof of the above via logging tools
Traditional data security focuses on point-to-point protection. Data is encrypted when it leaves System A, for example, then decrypted on System B for processing. The encryption-decryption sequence repeats when the data goes from System B to System C. Data may also be encrypted in flight. There’s no guarantee that these encryption processes are based around the same standard; in fact, there is no guarantee of encryption at all. Meanwhile, human factors present a risk, as always. Data Privacy Passports addresses these concerns using an approach known as data-centric audit and protection (DCAP).
DCAP replaces point-to-point security with an end-to-end model. With end-to-end protection, the raw data on the system of record (IBM z15 or IBM LinuxONE™ III) is transformed into what is known as a trusted data object (TDO). A TDO consists of an encrypted field with metadata that provides role-based access to the data as defined by a centralized policy. The TDO can be safely transferred to intermediate points while remaining fully protected throughout (see Figure 1).
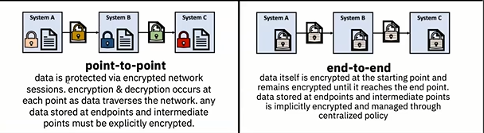
“The object that moves on the enterprise now retains the protection that it had to start with,” says Anthony Sofia, senior technical staff member, IBM Z. “It becomes irrelevant what protection is available in flight or as it lands on System B or C because that object itself has been fundamentally protected.”
Data Privacy Passports is based on a hardware component known as the passport controller that resides on the system of record. The passport controller enables any table to be protected on a field-by-field basis. Access to data tables by users is no longer binary. Instead, the data administrator uses the passport controller to configure a TDO to present different views to different users. A data owner responsible for quality and enforcement may have full access to all data, for example, while a data scientist might only have access to clear data fields for analysis but fields containing sensitive information would be masked.
Because TDOs provide platform-independent protection at all times, the technology is particularly effective for hybrid cloud deployments. Consider a company that has offloaded its marketing applications to a public cloud. The marketing department might request customer data in order to develop a new sales campaign. In many cases, they just need information like buying history, not other, potentially sensitive, information. The data could be packaged in a TDO and configured for a custom view.
“The passport controller would protect the sensitive information but not protect the clear information,” says Sofia. The sensitive fields are protected while the TDO is in the cloud. The marketing team could perform their analysis on the clear data to identify the customer subset for the email blast. “Those records would be brought back on premises to the controller, which would be able to decrypt the sensitive information and show the application the actual values,” he continues. “You can keep the data protected while it’s in the cloud and then unprotect the subset of data that comes back on premises.”
Data Privacy Passports and its TDOs are also useful for other types of shared infrastructure, such as AI. Companies are increasingly experimenting with AI as a tool for analytics and customer service. Although AI platforms are complex and capital-intensive, different lines of business within the same organization may still build out their own, out of concerns over data protection. Data Privacy Passports provides an alternative. “You can load the protected data into a shared infrastructure and then just dynamically provision a view of the data for each user,” says Sofia. “You can optimize your AI experimentation with respect to hardware usage and planning.”
Privacy and Revocation
Data protection is essential in our current business environment. It’s not sufficient, however, “Data security does not equal data privacy,” says Sofia. “You can’t have privacy without security, but you can have security without providing privacy.” Data privacy functionality is intrinsic to Data Privacy Passports. Once the centralized policy is established on the system of record, it’s “baked in” at the point of extraction when the raw data is converted to the TDO. Policy is then enforced at the point of consumption in a transparent and easily auditable fashion.
One of the ways Data Privacy Passports enforces privacy and protection at point of consumption is through its ability to remotely revoke privileges. When the passport controller creates a TDO, it stores the data encryption key for the TDO while embedding a corresponding key label in the TDO itself. Before data on the TDO can be decrypted, the key label needs to be matched to the data encryption key on a passport controller. This feature enables access to a TDO to be revoked remotely at any point in time. The feature is particularly useful for data breaches involving stolen login credentials or malicious employees. If any attempt is made to decrypt the data without the use of available encryption keys then the request to open that TDO will fail.
Fibre Channel Endpoint Security
IBM Z provides trusted data through pervasive encryption on the platform and the TDOs of Data Privacy Passports. It also supports trusted execution through containerization. But what if a server spoofing a legitimate storage network requests a TDO from the passport controller? The TDO might be sent to the server, where it would request the security key from the passport controller by presenting the key label, putting sensitive data in the hands of bad actors. To prevent this occurrence, IBM has added another layer of protection through Fibre Channel Endpoint Security. “An organization’s most sensitive data flows across Fibre Channel links, within data centers, through patch panel rooms, between buildings, and even between geographically distanced sites,” says Patty Driever, senior technical staff member, IBM Z Storage and Networking Technology and Strategy. “With a heightened focus on preventing insider breaches and complying with ever-increasing privacy standards, we created Fibre Channel Endpoint Security.”
Initially, Fibre Channel Endpoint Security was designed to authenticate a connection between IBM z15 servers and IBM DS8900F storage. Those capabilities may be extended to other end points in future. Fibre Channel Endpoint Security also encrypts the data flowing across the link, independent of user, application, or operating system. It ensures that the data exchanged between two data centers, for example, is passing between two trusted identities. The offering is a hardware-based solution that imposes no CPU overhead and has minimal impact on performance. Encryption can be verified and audited using additional display and logging support added in IBM Z operating systems such as IBM z/OS® and Linux®. Fibre Channel Endpoint Security substantially reduces the threat of unauthorized access to data in flight.
One of the key goals of the Fibre Channel Endpoint Security development team was ease of use. “Other existing security offerings enable a greater granularity of access control, but with that comes much more involved key management and access control set up,” says Driever. “We designed Fibre Channel Endpoint Security to provide broad coverage with easier and more efficient deployment.”
To simplify operations, the offering doesn’t require security administrators to perform any explicit key management, but simply to provide access to an external key server so that key management and distribution can be handled implicitly and securely by the solution. Once it’s enabled on a connection, all data flowing between the endpoints is secured. Finally, Fibre Channel Endpoint Security puts the emphasis on flexibility and customization. Security administrators can invoke protection for compatible equipment while also allowing connection to legacy servers and storage devices that are not security-enabled, if desired.
A Layered Approach to Data Security
In today’s regulatory environment, organizations are custodians, not owners, of the data they collect. They must protect that data from layered threats while ensuring privacy and maintaining compliance. IBM Z provides a comprehensive layered toolkit to help achieve this goal. Protection and privacy begin with pervasive encryption and trusted execution on the mainframe. Data Privacy Passports provides trusted data while Fibre Channel Endpoint Security ensures trusted endpoints and trusted connections. The combination enables organizations to maximize the usefulness of the data they hold while at the same time protecting it.