Kubernetes Container Security Best Practices With Red Hat Advanced Cluster Security for Kubernetes
As we work with organizations who are adopting containers as part of their software development strategy, we have seen container security become a challenge for many, and at times an aftersight. This is not on purpose, but primarily a result of the vast differences between the new technology of containers versus the virtualization model many organizations are familiar with. As container adoption grows, understanding how to properly secure containers within your software delivery practice becomes a very important task. Our goal throughout this article is to outline the top priorities to consider as your organization begins to develop its container security standardization strategy.
According to Sysdig, 54% of containers live for five minutes or less, which makes investigating anomalous behavior and breaches extremely challenging. This creates the need for cloud-native security and for organizations to have a plan to address container security risks immediately. Security needs to be at the forefront in the software delivery lifecycle (SDLC) to promote the adoption of cloud processes and proactively prevent security and compliance risks. With vulnerabilities uncovered daily and security threats surrounding us, it is critical for container security to become a top area of focus and best practice. Figure 1 shows some interesting findings from StackRox around current trends within container security.
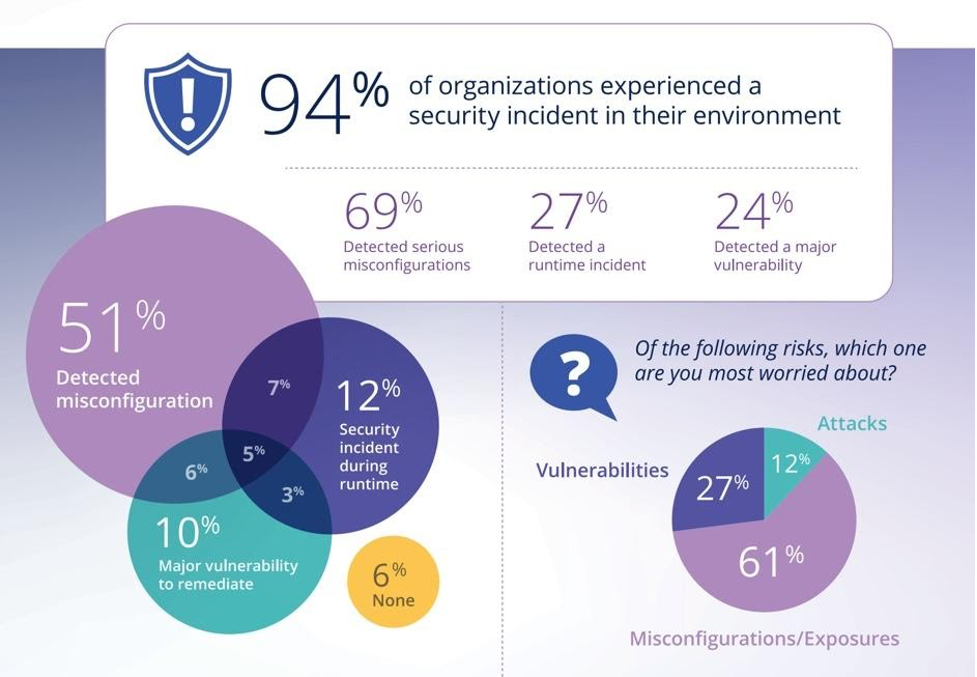
Container Security Best Practices
As your organization adopts container engines, such as Kubernetes, it’s important to understand container security best practices to help minimize the risk of security breaches. Here are some topics to consider as you plan for your container environment:
- First, make sure Kubernetes-native security architecture and access controls are in place:
- Restrict network access for your API control plane to only the IP addresses needed to administer the cluster eliminating public access points.
- Limit the access to etcd (the Kubernetes native key-value store) to only be accessible through the Kubernetes control plane.
- Encrypt all drives at rest.
- Next, secure your configurable cluster components:
- Set up Role Based Access Controls (RBAC) to ensure proper access limitations. When doing so, avoid Kubernetes defaults.
- Integrate with your standardized authentication system.
- Select a solution for application secrets management.
- Set up your pod security controls through Kubernetes.
- Set up cluster resource restrictions to ensure load requirements are not exceeded.
- Make sure the proper network policies are in place. Specifically enforce default deny networking rules in Kubernetes namespaces.
- Next, secure the application/ services that run on your cluster:
- During the image build process, make sure a security vulnerability test is being run to help ensure compliance has been met.
- Adopt a private container registry to host vetted and secure golden images. Build images from scratch or ensure image base layers are from a trusted source. This step is important to ensure best practice versus the risky practice of pulling images down from the web that may have vulnerabilities.
- Make sure your Kubernetes environment does not allow privileged users.
- Lastly, implement testing best practices to ensure compliance throughout the SDLC:
- Some examples include pre-layer scanning to scan OS packages, binary fingerprinting, running file content tests to test for vulnerability and open-source license checking, runtime vulnerability detection.
Red Hat Advanced Cluster Security for Kubernetes
Solutions like Red Hat Advanced Cluster Security for Kubernetes (ACS), which is based on the StackRox technology, were created for this new enterprise challenge. Visual reference showing real life security data is depicted in Figure 2, below.
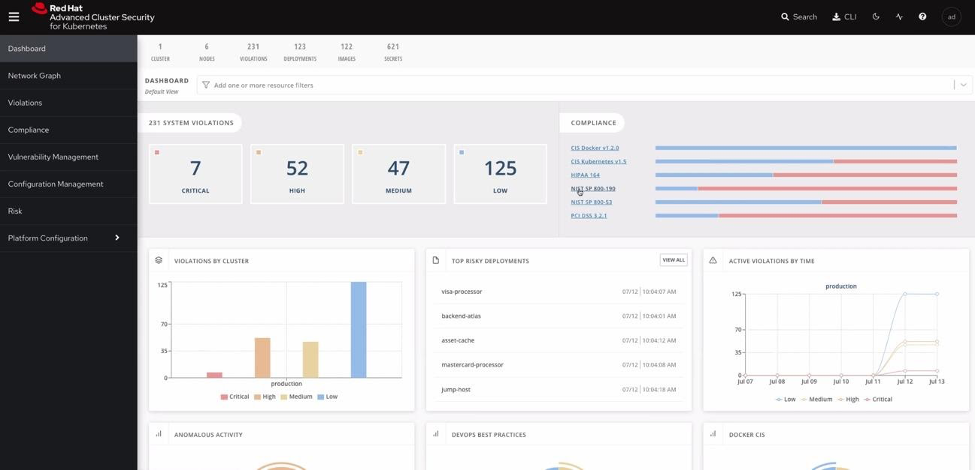
ACS helps in six critical areas:
- Vulnerability management in images and running containers
- Configuration management of deployments with security best practice top of mind
- Gaining context and critical data through risk profiling
- Network segmentation with isolation and access controls for individual applications
- Compliance auditing to meet contractual and regulatory requirements
- Detection and response to address active threats in organization’s environments
The main takeaway is that ACS is able to reduce an organization’s risk profile in their Kubernetes deployments. Coupled with Red Hat Quay, Red Hat’s container registry scanner, organizations can help ensure security throughout their environment.
Red Hat Advanced Cluster Security for Kubernetes offers an interactive dashboard to create easy audit reports which can be used to examine compliance regulations like HIPAA requirements, PCI and CIS benchmarks. ACS also helps with network segmentation. Corporations are pushing to separate or segment their networks to provide hop-to-hop security in order to limit privileges and reduce the likelihood of an attack. Using Kubernetes-native controls, organizations can visualize network traffic and enforce network segmentation more seamlessly.
Risk prioritization is another important consideration. ACS provides the ability to see your container deployments and provides a ranking by risk level. Configuration management gives organizations the ability to strengthen and harden Kubernetes environments, leading to a reduced likelihood for attacks.
The Cost of Data Breaches
The cost of data breaches in 2021 continue to be staggering in nature. According to a report by Varonis/IBM the healthcare industry is the most expensive industry for a data breach at $7.13M. An average from a global perspective was $3.86M per data breach. In most situations, it takes time to discover the data breach and because of this, 39% of the costs associated with a data breach occurs more than a year later. The country with the highest average total cost of a data breach is the United States at an amazing $8.64M.
With the laser beam focus that remains on all facets of security, container security remains at the forefront of this discussion. The success of the entire environment is key to quality construction of applications and also key to the success of the organization.
At the center of this systemic shift is the open source container orchestration system Kubernetes. Kubernetes is the de facto standard for automating the deployment and management of cloud-native applications in production. This is depicted in Figure 3, below.
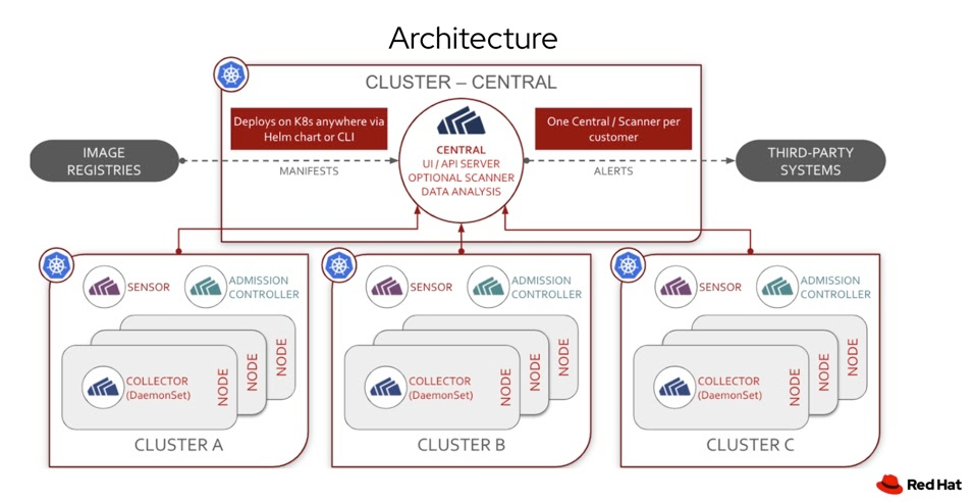
With modernization topics such as container security, Red Hat Advanced Cluster Security for Kubernetes is proving to be a formidable solution for container security and a strong player within the security space, adding extremely beneficial compliance guardrails to make sure the needed security and compliance is being met throughout the SDLC process. Check out this Red Hat Advanced Cluster Security for Kubernetes whitepaper to learn more.