Are You Following the ‘Big 3’ Basics of Cybersecurity?
Security consultant Niall Ashley explains the importance of role-based access control, zero trust and least privilege

Hot on the heels of the M&S and Co-op cyberattacks in the UK, it was reported by CNN that “Scattered Spider” hackers were also targeting U.S. retailers including Ahold Delhaize USA. In an age when the global economy revolves around digital technology, data is one of the most valuable commodities on the planet. And where valuable data is found, hackers will seek to infiltrate, extract and extort it.
The reasons behind cyberattacks, which range from ransomware and phishing to denial of service and zero-day exploits, are many and varied. Criminal extortion and financial benefits are the most obvious. But you also have state-sponsored attacks and espionage, ideological reasons (a.k.a. hacktivism), intentional sabotage and plain old revenge.
Irrespective of the motive, we need to be aware of the threats, and work to keep our data as secure as possible. One of the fundamentals is making sure we adhere to three basic principles of cyber security: role-based access control, zero trust and least privilege.
Role-Based Access Control (RBAC)
RBAC, sometimes referred to role-based security, is a mechanism that restricts system access. With RBAC, employees’ job roles should correlate with the levels of access they have, and it should be used in conjunction with resource classification. Consequently, employees are only allowed to access the information that is necessary to effectively perform their job duties, which better protects sensitive data.
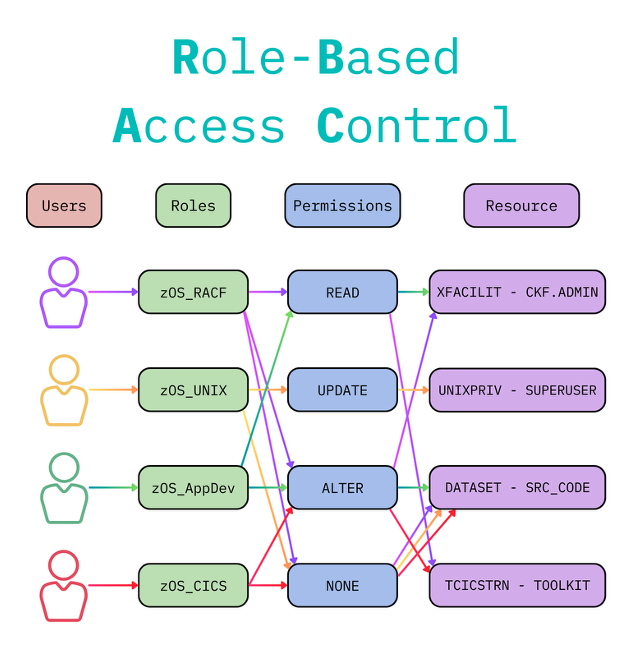
Figure 1. Role-based access control should be granular: different users, from different teams/departments, having different permissions to different resources.
Because many large organizations allocate their people into different departments and teams, access can be set up to coincide with the responsibilities of such groups. Roles can be based on several factors, such as responsibility (e.g., security), authority (e.g., manager), job level (e.g., junior) and so on.
For example: Bob has the job title senior security manager, and therefore may be connected to three different groups/roles. Each of these roles may grant different access permissions to resources, individually allowing access to read different datasets, alter a resource, or control a function.
The next two principles of cyber security have a number of similarities as well as differences.
Zero Trust: Trust No One
This security model is based on the principle of “Never trust, always verify.” It establishes strict access controls, wherein verification is required for every access request. Every user and device must be authenticated before being granted access to any resources. Examples include privileged access management (PAM), multi-factor authentication (MFA) and one-time passwords (OTP), and these may also use biometrics.
Least Privilege: Only What You Need
This approach limits user access to the absolute minimum level that is required to perform their job functions, and only allows users to access the resources they need, when they need them. By limiting user access in this way, organizations are in position to prevent unauthorized access to sensitive systems and data, reducing the risk of cyberattacks and data breaches. For example, a hospital receptionist will need access to book appointments for patients but should not have access to view their case files.
So, what are similarities and differences between zero trust and least privilege?
Both strategies are designed to protect access points and control access to systems. And both strategies were designed to minimize risk or cybersecurity breaches to systems by following practices of trust removal and/or access limitation.
Zero Trust uses the “trust no one” concept, seeing every user as a potential threat, justifying the need for verification and authentication of all users. Conversely, least privilege doesn’t necessarily authenticate; it simply restricts access to “only what you need” and “only as long as you need it.”
Lock Up Your Data: Follow Every Principle
In an ideal world, organizations will be following all three principles as a basic requirement. With zero trust, users will not be trusted by default, only being allowed access once they are verified and authenticated. With RBAC, users will be connected to groups that correlate with their responsibility, authority and competency (e.g., trainee database administrator). And with least privilege, each group that the user is connected to will have the absolute minimum access required, and access will only last for as long as is deemed necessary.
Unfortunately, we don’t live in an ideal world. While all this may sound relatively straightforward, in practice these principles are not always followed, or not in the ways they should. But if you think about your data as money, something with a huge current and potential value, and your systems as the bank vaults where you store that valuable currency, the importance of these principles becomes very clear indeed. In a bank, who has unfettered access to the most secure vaults or safe deposit boxes?
The reality is that you cannot afford a data breach, so you must endeavor to deploy RBAC, zero trust and least privilege security models as effectively as you can.