Dissecting z/OS Security Software—Base Elements, Optional Features and Products
In this edition of "z/OS and Friends," Joe Gulla turns his attention to z/OS security software, discussing more than 20 components of the stack

Security on enterprise computers is interesting, detailed and, at times, challenging to understand, especially for IT practitioners that are not security specialists. In my last article, I focused on security features on z/Architecture machines with an emphasis on hardware. This article is about security software.
You might ask: How can you separate hardware from software when it comes to security implementation? You are right, especially regarding system-level activity like security routines. It is somewhat artificial to separate the two because they frequently work together to make an outcome possible. So why do I separate the two? The answer is simple—the hardware and software do have individual identities with a necessary overlap in executing security procedures. So, it is partly a justifiable division. Also, it is an effort to make the topic more understandable by breaking it into these two main parts.
Let’s get into the details. If you add up all the software components—base elements, optional features and security products—more than 20 are discussed in this article. I have attempted to be comprehensive but I have not included non-IBM products, which would undoubtably make this coverage of the security challenge more complete.
Figure 1 below shows the z/OS software—base elements and optional features—that I will explain and explore in the first two parts of this article.
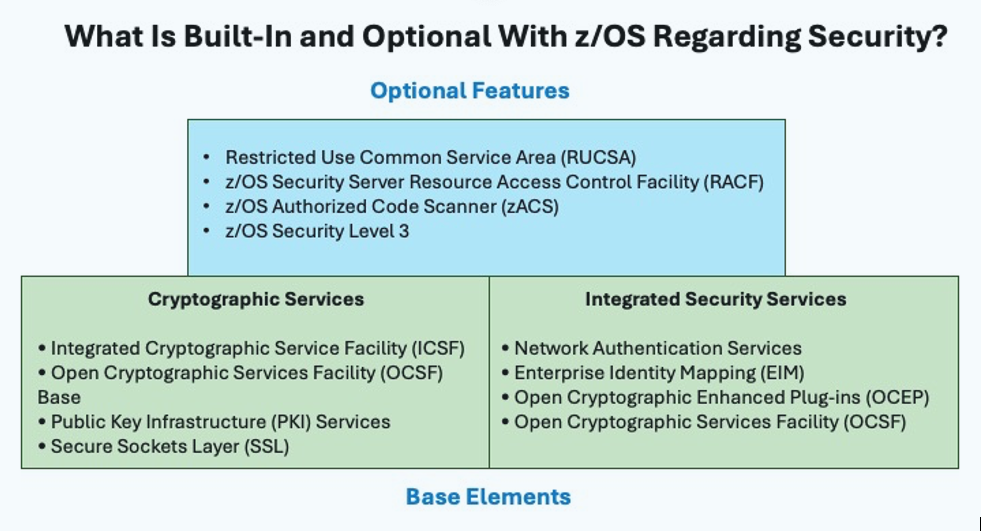
Figure 1. Base elements and optional features that are part of z/OS.
z/OS Base Elements Providing Security Functions
z/OS base elements are built in and provide foundational security capabilities. Providing backing for secure use of resources is important to most operating systems and is particularly important to z/OS. IBM has built into the OS significant support for a variety of important security techniques and standards. Let’s start with Cryptographic Services.
z/OS Cryptographic Services
Enterprises use the components of this base element of z/OS for the transformation of data to conceal its meaning. In z/OS, the base element Cryptographic Services provides functions including data secrecy, data integrity, personal identification, digital signatures and the management of cryptographic keys. Cryptographic Services includes four collections of software:
1. Integrated Cryptographic Service Facility (ICSF)
Integrated Cryptographic Service Facility (ICSF) is a software element of z/OS that works with hardware cryptographic features, like Crypto Express cards, to provide secure, high-performance cryptographic operations. It supplies Cryptographic APIs for applications to perform encryption and decryption, digital signatures, key generation and management, hashing and message authentication and hardware Integration. In short, it provides a framework of cryptographic services.
2. Open Cryptographic Services Facility (OCSF) Base
The Open Cryptographic Services Facility (OCSF) Base is a component of IBM’s z/OS Cryptographic Services, which provides a framework for integrating cryptographic functions into applications running on IBM mainframes. It provides the following base cryptographic functions: data secrecy, data integrity, personal identification, digital signatures, and management of cryptographic keys.
3. Public Key Infrastructure (PKI) Services
IBM z/OS includes Public Key Infrastructure (PKI) services as part of its security framework. These services are primarily provided through components including those found in Table 1.
Table 1. Components of z/OS PKI Services
| Component | How Used |
| RACF Digital Certificate Support | Resource Access Control Facility (RACF) on z/OS supports digital certificates (X.509 format), Certificate Authorities (CAs), key rings for managing certificates and support for SSL/TLS in conjunction with other subsystems like FTP, TN3270 and HTTP. |
| Integrated Cryptographic Service Facility | Integrated Cryptographic Service Facility (ICSF) provides cryptographic services, including key generation and management, digital signature creation and verification and encryption/decryption using public/private key pairs. |
| z/OS PKI Services | PKI Services is a separately installable feature that provides a web-based CA for issuing and managing digital certificates, support for X.509 certificates, integration with LDAP directories, certificate revocation lists (CRLs) and web-based administration and user interfaces. |
| z/OS Management Facility) | z/OS Management Facility (z/OSMF) is not a PKI service itself but can help manage and configure security services, including certificate management tasks. |
4. Secure Sockets Layer (SSL)
The z/OS Communications Server for TCP/IP supports the AT-TLS function in the TCP/IP stack for applications that require secure TCP/IP connections. AT-TLS performs TLS on behalf of the application, such as Db2, by invoking the z/OS system SSL in the TCP layer of the TCP/IP stack. Enabling it is explained here.
This is the end of the discussion of z/OS Cryptographic Services. Next, I’ll explain Integration Security Services, which is the second grouping of z/OS Base Elements for security.
z/OS Integrated Security Services
z/OS Integrated Security Services (ISS) provides a comprehensive set of security features for the z/OS operating system, enhancing security for applications, data and network access. Integrated Security Services includes four components that make up the service as discussed in Table 2:
Table 2. Components of z/OS Integrated Security Services
| Network Authentication Services | Network Authentication Service (NAS) is IBM’s implementation of the Kerberos protocol on z/OS. It allows secure authentication of users and services in a distributed environment without transmitting passwords over the network. NAS integrates with RACF to manage user credentials and access control policies. |
| Enterprise Identity Mapping | Enterprise Identity Mapping (EIM) on z/OS is an IBM infrastructure technology designed to simplify identity management across heterogeneous systems and applications. EIM allows organizations to map user identities across multiple systems and user registries. This is especially useful in environments where users have different user IDs on different platforms like Windows, UNIX and z/OS. |
| Open Cryptographic Enhanced Plug-ins | z/OS Open Cryptographic Enhanced Plug-ins (OCEP) is a component of IBM’s z/OS Integrated Security Services that enhances cryptographic capabilities for applications by providing secure access to digital certificates and private keys stored in the RACF database. OCEP is a set of service provider modules (plug-ins) designed to work with the OCSF framework on z/OS. |
| Open Cryptographic Services Facility | z/OS OCSF is a flexible and extensible framework within IBM z/OS that provides standardized access to cryptographic and security services for applications running in the UNIX System Services (USS) environment. OCSF is IBM’s implementation of the Common Data Security Architecture (CDSA), originally developed by Intel. It allows applications to access cryptographic services like encryption, decryption, digital signatures and certificate management, through a modular and pluggable architecture. |
Two other z/OS base elements have a relationship to security. System Management Facilities (SMF) collects and records system and security-related events for auditing. SMF record type 83 records security events. Additionally, z/OS USS provides UNIX-style file permissions and access control. This is the end of the discussion of z/OS Base Elements pertaining to security.
Next, let’s explore z/OS optional features that support the security discipline.
z/OS Optional Features Providing Security Functions
Providing support for secure use of resources is particularly important to z/OS. IBM has built into the OS significant support for a variety of important security techniques and standards. Four optional features extend the security support in z/OS and are discussed below.
1. Restricted Use Common Service Area (RUCSA) in z/OS
Enterprises use this optional feature if their installations cannot eliminate user key (8-15) common storage usage. RUCSA provides a means of isolating user key common storage to specific users. By doing so, it controls or eliminates the security risk that is associated with common user key storage.
2. z/OS Security Server RACF
Enterprises use Security Server to control access to protected resources. Security Server contains one component named RACF, which uses the limited DES, CDMF, RC 40-bit, RSA and DSA algorithms for encryption.
What is the Difference Between the z/OS Security Server and RACF?
The z/OS Security Server and RACF are closely related components in IBM’s z/OS environment, but they are not the same. RACF is a software product developed by IBM that provides security services on z/OS. The z/OS Security Server is a broader component of the z/OS operating system (an optional feature) that includes RACF as its core. Additionally, it provides a framework for security services on z/OS, including interfaces for external security managers (ESMs), support for System Authorization Facility (SAF) and security APIs and services for applications.
3. z/OS Authorized Code Scanner (zACS)
Enterprises use zACS as it dynamically scans authorized code and provides diagnostic information for subsequent investigation as needed. The zACS feature is entitled when you purchase the separately priced product, IBM Threat Detection for z/OS.
4. z/OS Security Level 3
Enterprises use z/OS Security Level 3 because it provides stronger encryption for z/OS. Stronger encryption generally means greater than 64 bits, which makes the encryption harder to crack. z/OS Security Level 3 was first delivered with z/OS V2R4. It is discussed in this comprehensive list of base elements and optional features. The components in this feature that have greater than 64-bit solutions include:
Table 3. Components of z/OS Security Level 3
| Communications Server Security Level 3 | Works with the Communications Server base element to provide stronger encryption. |
| IBM Security Directory Server (SDS) Security Level 3 | Works with the IBM SDS base element to provide stronger encryption. This component uses the RC4, TDES, and Advanced Encryption Standard (AES) algorithms for encryption. |
| Network Authentication Service Level 3 | Works with the NAS component of the Integrated Security Services base element. This component uses the Triple Data Encryption Standard Triple DES (TDES) and AES algorithms for encryption. |
| System Secure Sockets Layer (SSL) Security Level 3 | Works with the System SSL component of the Cryptographic Services base. This component uses the RC2/RC4, TDES and AES algorithms for encryption. |
This is the end of the discussion of z/OS optional features pertaining to security. Next, let’s explore security products for z/OS from IBM.
IBM Products Supporting Security on z/OS
There are several separate IBM products that integrate with z/OS to provide advanced security. Of course, it is not as simple as “runs on z/OS” and “supports z/OS systems and applications.” Some products run on z/OS and support z/OS, whereas others run on z/OS but help to monitor and manage other systems in addition to z/OS. Still others run elsewhere and include inputs from z/OS or software that runs on z/OS.
The products listed in Figure 2 answer the question: What IBM products support the security discipline for z/OS? Please note that these products typically run apart from or in support of the base elements and optional features, and they reflect a variety of software implementation choices.
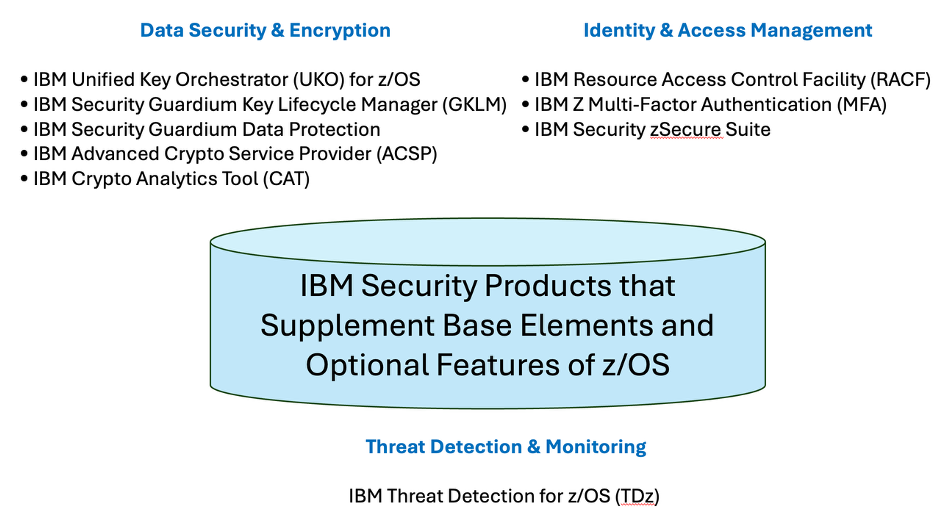
Figure 2. IBM security products to be explored.
IBM offers a comprehensive suite of products that support the security discipline for z/OS, covering areas such as data security and encryption, identity and access management, and threat detection and monitoring. Here are some of the key IBM security products:
Data Security and Encryption
There are five products in this category. They are discussed in Table 4 below.
Table 4. Products that Support Data Security and Encryption
| IBM Unified Key Orchestrator (UKO) for z/OS | UKO is a key management service that provides users with management capabilities for pervasive encryption for IBM Z as well as “keep your own key” capability for cloud data encryption. |
| IBM Security Guardium Key Lifecycle Manager (GKLM) | GKLM manages encryption keys throughout their lifecycle. It can manage encryption keys for IBM z/OS, but it does so indirectly through integration with supported hardware and software components. GKLM provides centralized key management using standard protocols like KMIP, IPP and REST APIs. While GKLM itself is not installed on z/OS, it can manage encryption keys for z/OS environments. |
| IBM Security Guardium Data Protection (GDP) | GDP is data security software in the Guardium family of products. GDP monitors data access, automates compliance auditing, and detects threats. It has support for some system software that runs on z/OS, like Db2. |
| IBM Advanced Crypto Service Provider (ACSP) | ACSP is a solution that allows distributed clients to access cryptographic services and hardware on IBM Z systems remotely. It essentially provides a “crypto-as-a-service” model, enabling applications on various platforms like AIX, Linux, Windows and even cloud environments to utilize the robust cryptographic capabilities of IBM Z. |
| IBM Crypto Analytics Tool (CAT) | CAT collects and analyzes cryptographic security information to detect anomalies and ensure secure encryption. After inventory collection, CAT helps organizations analyze their cryptographic security posture, identify vulnerabilities and ensure compliance with security policies and best practices. |
Identity and Access Management
There are three products in this category. They are discussed in Table 5 below.
Table 5. Products that Support Identity and Access Management
| IBM Resource Access Control Facility (RACF) | RACF is a core z/OS component for controlling access to system resources, playing a critical role in enterprise security by controlling access to system resources. RACF is designed to: Authenticate users to verify their identityAuthorize access to resources like files, datasets, programs, etc. Audit access attempts and changes to security settings A key concept in understanding RACF is users and groups. Users are defined with unique IDs. Groups allow collective management of permissions. |
| IBM Z Multi-Factor Authentication (MFA) | MFA adds an extra layer of security for user authentication. MFA secures user logins to z/OS, z/VM and Linux on Z. It helps mitigate the risk of compromised passwords with expanded authentication capabilities for IBM Z and LinuxOne environments. |
| IBM Security zSecure Suite | This software provides auditing, compliance reporting and real-time monitoring of RACF and other security settings. IBM zSecure portfolio enhances IBM Z environments by adding layers of assurance like audits, alerts, administration, reporting and authentication. In addition, it automates tasks, detects threats, issues alerts and ensures compliance for better efficiency and error reduction. |
“What About?” Questions to Help Describe RACF
Want to dig a little deeper into RACF? The questions in table 6 below help to better understand what RACF is about.
Table 6. Questions Designed to Help Better Understand RACF
| What about resources? | RACF protects datasets, transactions, terminals and more. Resources are categorized and controlled via resource classes. |
| What is an Access Control List (ACL)? | The ACL is a tool used to define which users or groups can access a resource—and at what level, like read, write and execute. |
| What are profiles? | RACF uses discrete and generic profiles to manage access. Profiles define the rules for accessing resources. |
| What about security labels and levels? | RACF supports Mandatory Access Control (MAC) using security labels for classified environments. |
| What about integration and extensibility? | RACF integrates with other IBM security tools like zSecure and Tivoli. It can work with LDAP, Kerberos and digital certificates for modern authentication. Note: LDAP Servers, like IBM Tivoli Directory Server for z/OS, supports centralized directory services for identity and access management. Also, Network Authentication Service, which includes Kerberos, is available on IBM z/OS. Kerberos on z/OS is part of the Network Authentication Service component. It provides strong authentication for client/server applications using secret-key cryptography. |
| What about auditing and compliance? | RACF logs all access attempts and changes. It supports compliance with standards like SOX, HIPAA and PCI-DSS. |
To recap: RACF is important for mission-critical environments like those used in banking, government and large enterprises. It offers granular control necessary to fine-tune access management. It has both legacy and modern support as it bridges traditional mainframe security with modern identity management.
Threat Detection & Monitoring
IBM Threat Detection for z/OS (TDz) makes use of artificial intelligence to bring the detection of anomalous, potentially malicious data access to the z/OS platform. Its outputs enable diagnosis and response.
These nine IBM products supporting security on z/OS work together to provide end-to-end protection for z/OS environments, ensuring compliance with industry standards and defending against both internal and external threats.
What is Next?
Next month, I will cover networking in z/OS with two articles. I’ll be focused on protocols like VTAM and TCP/IP, as well as networking products and components like z/OS Communications Server and HiperSockets. I’ll also survey management and monitoring tools like NetView and RMF, and look at security integration with Application Transparent Transport Layer Security and Intrusion Detection Services (IDS).