The Glass Is More Than Half Full: From Attack to Defense
Vertali’s Mark Wilson discusses why it’s time to change the mindset around mainframes and cyber threats—making the platform part of every cybersecurity conversation in the organization
I’ve been in the mainframe space for more than 40 years. During that time, I’ve seen firsthand the underinvestment in the platform and the teams that support it. We’re continuing to deal with the fallout from that—primarily a continuing skills shortage as experienced mainframers retire while too few newbies come through the pipeline. And all in the face of a cyber threat landscape that’s changed radically and expanded greatly in the past few years.
But I’m an optimist, a glass-half-full person, and believe we should accentuate the positive: Turn that frown upside down. Or, as George Soros puts it better, “The worse a situation becomes, the less it takes to turn it around—the bigger the upside.” And there are many, many upsides to be had.
The mainframe has been modernized, undergoing something of a renaissance. As I’ve said many times, it remains the system of record and transactional beast of burden, the heart of so many organizations and sectors. Including critical national infrastructure. And we should never forget that it remains the most securable platform on the planet; it just doesn’t come that way out-of-the-box. In which case, we need to get on with securing it. Easier said than done, you might say. But I’ve seen it done. It may require a change in thinking.
Securing the Modern Mainframe
We need to stop fretting about the possibility of cyber attack. What I mean is: We have a big target painted on us, and it will happen. Instead, we need to focus on practical steps to mitigate the risks, to defend and protect the mainframe properly. This means moving from a responsive “attack mindset” to ensuring a robust and resilient defensive stance. To do that, the mainframe must be included in all cybersecurity conversations in the organization. As those conversations will inevitably involve the three key elements of people, process and technology, mainframe security needs to be considered in light of those elements too.
It’s always worth referring to the U.S. government’s National Institute of Science and Technology’s (NIST) Cybersecurity Framework (CSF). NIST characterizes cyber resiliency as being able to “anticipate, withstand, recover from and adapt to adverse conditions, stresses, attacks or compromises.” It’s accepted that an attack is no longer a case of if but when. So, instead of focusing efforts on keeping criminals out of the network, is it more practical to assume they’ll eventually break through our defenses and develop a strategy to reduce the impacts and accelerate recovery?
It’s long accepted that cybersecurity isn’t only a technical challenge solved by acquiring technical solutions, but a pressing business issue that has to be tackled (and funded) across people, processes and technology. Such thinking is especially pertinent for the mainframe, given the platform’s maturity and widespread complacency based on the misplaced belief that it’s inherently secure, as well as learned habits, culture and the skills gaps. The NIST framework is one way to approach this, focusing on:
1. Identify
2. Protect
3. Detect
4. Respond
5. Recover
This overarching process becomes an ongoing, virtuous circle.
Prevention Is Better Than Cure: What We Need To Do
Identify means properly understanding the risks. It means looking at data classification, data ownership, and reviewing our policies and standards. Are we getting the best out of our current tools, and should we be investing in new ones? What about the organizational mindset and culture? What is the true skills gap, and how can we close it? Is there an up-to-date understanding of the evolving threat and vulnerability landscape? Are we properly enabling and supporting the security operations center? We need to discover answers to these questions.
Protect could also be termed “limit and contain.” We need to work the tools that we have, making use of advanced analytics, real-time alerts and more. We need role-based access controls (RBAC) and privileged identity and access management solutions, part of a strategy and approach that has various tools and approaches focused on zero trust. We also need to look at subsystem security (e.g., CICS, Db2, MQ, Automation) and review and amend legacy application security controls. In terms of our people, we need to perform process reviews and ask why controls degrade. It’s also worth reviewing staff awareness campaigns in a mainframe context.
Detect is about timely discovery. This means, for example, real-time alerting (making increasing use of AI and machine learning) as well as file integrity monitoring (FIM), behavioral analysis, network discovery and forensics and other techniques. At the same time, a key part of cyber resiliency is validating the backups that we take: Are they any good?
Respond is knowing what to do when bad things happen. When it comes to cyber resiliency, we need to create a strong plan, then build the most effective approach, test, update, test again and keep testing. And what about recovery planning? What would we actually do if we encountered a serious issue? This leads into Recover, aka restore, review, re-plan, another key aspect of cyber resiliency planning. For example: If we’re recovering and restoring after a particularly nasty ransomware attack, our backups had better be good (threat free), or we risk being open to exactly the same backdoors and attack as before.
All of this requires the right staff, the right processes and the right tools. It also means there’s an awful lot to do in multiple areas, from IMS, Db2, CICS and RACF to Automation, job scheduling, source code management, storage management, network security, forensic analysis, file integrity monitoring … but it’s not Mission: Impossible. In the sense that we won’t need to ride a motorcycle off a mountain and parachute onto a moving Orient Express. (Then again, I don’t know about your specific mainframe setup, so I can’t be 100% certain about that.)
Mission: Possible – Should You Choose To Accept It
“The world is changing,” as movie trailers often say. Cyber threats are evolving, and vendors are working hard to come up with solutions. On our side, we need to step back and take a long hard look at our systems and networks. The mainframe no longer exists in splendid isolation. We have to decide what’s right for our own sites. And while we do need to consider multiple aspects across people, process and technology, that doesn’t mean attempting to do everything at once.
Another way to look at this, to make sense of what we need to do, is to formulate a new security roadmap for the organization. One that treats the mainframe as simply another vulnerable element of the enterprise infrastructure and makes it part of the conversation. For example:
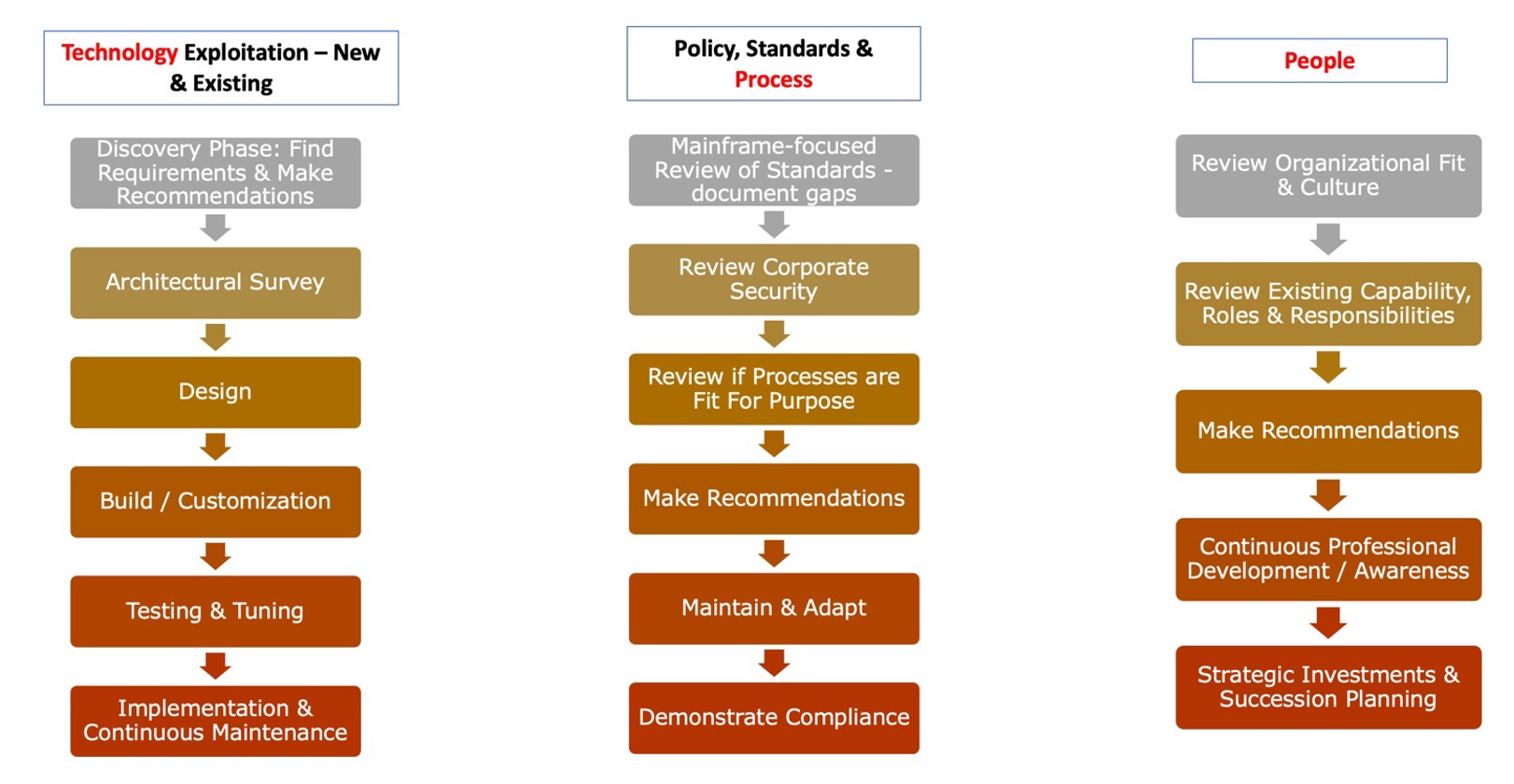
It all starts with a well-thought-out cybersecurity/resiliency plan aligned with a strategy that addresses your specific site needs AND reflects the NIST framework of identify, protect, detect, respond and recover. Regular testing of everything is a must. We need to ensure we’re building or using tools and processes that work for our specific environment. We need to do this all step-by-step, focusing on the issues to be resolved and the gains to be made, and recognizing these steps will be different for everyone. Finally, we have to accept this will all take time.
When it comes to mainframe cybersecurity and resiliency, I do believe that our glass is already more than half full. Our job is to fill it up, right to the brim.