Networking on z/OS: Something for Every Enterprise
In this edition of "z/OS and Friends," Joe Gulla traces the evolution of networking on z/OS and explores the associated architecture, protocols and products

Networking on z/Architecture systems running z/OS is a robust and highly integrated environment. IBM has been working on this for decades, fueled by customer wants and needs, and it shows it. There are many networking choices and approaches to utilize with z/OS in support of enterprise-grade communication. Known for its security and scalability, mainframe networking has a dynamic history that started with what we now consider elementary approaches and protocols.
Today, z/OS on the latest z/Architecture servers encompasses a cumulative software stack that includes most of the history of telecommunications innovations, right up to the present. Networking on z/OS evolved from early protocols to System Network Architecture. Later, TCP/IP was fully embraced and utilized. Today, networking on z/OS is still growing and changing.
Visiting the Rail Yards to Learn Something, Anything …
I got my start with networking in the late 1970s. I was sent on a field trip by my employer, a freight railroad, and I got to see what IT looked like in the rail yards. What I saw was the IBM 2741 printing computer terminal, which was introduced in 1965. It was right in the middle of everything, and was used a lot because nothing came in or out of the yard without messages with details about the engines and cars.
The 2741 looked like a fancy typewriter that could send and receive messages and data. The device used start-stop asynchronous protocols (ASC) but these were not formalized as complete communication protocols for mainframes. They were more like electrical signaling standards for teletype-style communication. This is what I found looking back recently and doing research. At the time, I was a COBOL programmer trying to improve car handling in the freight yard by automating manual procedures. Process reengineering, making the process more efficient, wasn’t yet a goal as it was years later.
What Did an Early Protocol Look Like?
The earliest formal communications protocol used by IBM mainframes was Binary Synchronous Communication (BSC), introduced to support remote job entry and terminal communication. It was widely used with devices like the IBM 2780 and IBM 3270 terminals. In my first couple jobs I got to experience ASC and BSC, as well as various 3270 terminals and other OEM devices and displays. These early protocols had error recovery but were somewhat unreliable. Typically, the data was transmitted over telephone lines (leased lines). The lines had dedicated bandwidth and generally consistent performance. Although they were not shared with other customers, there were often challenges with availability. The communication systems programmers in those days spent a lot of their time providing support to network operations and working with the line carriers.
What About Display Terminals?
In my workplace in the IT department, our 3270 terminals were connected to the mainframe through IBM 3274 control units which were tucked into the computer room. They acted as terminal concentrators. Coaxial cables were run through the walls and ceiling to connect these devices on both ends. Reliability was better than leased phone lines. Speed was better too, much better. There were occasional failures on the 3274s; service was called and fixes were made. This was the time when I first learned the phrase “card swap,” a technique used to get the controller up and running by moving existing circuit cards around the device. So, availability in the 1970s, even on local devices, was not 100%. That was my experience, but my employer in those early days was a cash-strapped, bankrupt railroad.
Getting Serious—Architecture, Protocols and Products
Let me start with a breakdown of what networking encompasses, focused on architecture, protocols and products. At present, the TCP/IP Stack is the focus of z/OS networking. TCP/IP implements standard internet protocols—for example, IPv4, IPv6, TCP, UDP and ICMP—and provides socket APIs for applications to communicate over the network. Virtual Telecommunications Access Method (VTAM) is a long-standing access method and is still widely used. VTAM manages Systems Network Architecture (SNA) communications. VTAM also interfaces with TCP/IP for hybrid environments. While VTAM and SNA are still supported for long-standing applications, most new development and integration with distributed systems rely on TCP/IP. New developments utilize web services, cloud and REST APIs, as examples.
The product IBM Communications Server for z/OS integrates TCP/IP and VTAM. It provides services like policy-based networking, IP Security (IPSec) and Intrusion Detection Services (IDS). Network Device Interface (NDI) is also supported. It abstracts hardware-level network interfaces and supports Open Systems Adapter (OSA-Express) for high-speed ethernet.
Core Protocols—Network and Application
TCP/IP on z/OS
Configuration basics involve TCPIP.DATA, PROFILE.TCPIP definition files. IPv4 and IPv6 is supported with both dynamic and static configurations. TCP/IP configurations can be set up as either dynamic or static, primarily referring to how IP addresses are assigned to devices on a network.
SNA and VTAM
Systems Network Architecture and Virtual Telecommunications Access Method are foundational technologies in IBM mainframe networking. While they may seem legacy by today’s standards, they remain critical in many enterprise environments due to their reliability, integration and support for mission-critical applications.
What Is the Specific Role of VTAM?
VTAM is the software component in z/OS that manages SNA communication. It acts as the SNA access method, enabling applications to communicate over SNA networks. Its importance can be summarized in Table 1, below:
Table 1. VTAM Functions and the Functions They Support
| Functions | What it Does |
| SNA Session Management | VTAM handles session establishment, routing and termination for SNA applications |
| Application Interface | Provides APIs for applications such as CICS, IMS and TSO to communicate over SNA |
| Network Control | Manages logical units (LUs), physical units (PUs) and network nodes, ensuring efficient communication |
| Support for Enterprise Extender | VTAM enables SNA applications to use IP networks via the Enterprise Extender product, bridging legacy and modern infrastructure |
Application Protocols
Here are three grouping of application protocols that are key to understanding what we experience in networking on z/OS today. The first grouping is FTP, Telnet and SSH.
FTP, Telnet and SSH
FTP, Telnet, and SSH—three classic network protocols used for remote communication and file transfer. The purpose of File Transfer Protocol (FTP) is to transfer files between a client and a server over a network. It is not secure by default—data, including passwords, is sent in plain text, however there are variants that add encryption. Teletype Network (Telnet) provides a command-line interface for remote login to another computer. Because of security shortcomings, it is largely replaced by Secure Shell (SSH). It is often used for legacy systems and network device configuration. SSH securely logs into remote systems and executes commands.
What About HTTP/HTTPS and Web Services?
Hypertext Transfer Protocol (HTTP) is the foundation of data communication on the web. It transfers data between a client (like a web browser) and a server. It is not secure. HTTP Secure (HTTPS) is a secure version of HTTP.
Web services are software systems that allow different applications to communicate and exchange data over the internet. Simple Object Access Protocol (SOAP) is a type of Web Service which is XML-based. It uses formal contracts based on the Web Services Description Language (WSDL) and it is often used in enterprise environments. Representational State Transfer (REST) is another type of Web Service. It is lightweight and flexible. It uses standard HTTP methods like GET, POST, PUT and DELETE, and it often returns data in JSON or XML. It is widely used in modern web and mobile applications.
SMTP and Email Integration
Simple Mail Transfer Protocol (SMTP) is the standard protocol used to send emails across the internet. It’s part of the application layer of the TCP/IP protocol suite and is used by email servers and clients to send, relay or forward messages. Email integration refers to the ability of applications or systems to send, receive and process emails automatically using protocols like SMTP, IMAP or APIs.
Networking Products on z/OS ‘Mean Business’
My dad used the phrase “means business” when he was giving something or someone high praise. The phrase fits when discussing the networking products from IBM on z/OS.
What Is IBM Communications Server?
IBM Communications Server for z/OS is a robust, enterprise-grade networking product that provides a comprehensive suite of communication protocols and services for IBM’s z/OS operating system. It plays a critical role in enabling secure, scalable and high-performance network connectivity for mainframe environments.
The core features of IBM Communications Server include support for both SNA and TCP/IP protocols, allowing legacy and modern applications to coexist. It enables communication with a wide range of platforms and devices. The product provides high availability and scalability. It is designed for mission-critical workloads with features like dynamic VIPA, Sysplex Distributor and automatic workload balancing. It provides integrated security with z/OS security services like RACF for authentication and access control. It also supports IPSec, TLS/SSL and AT-TLS for secure communications. Additionally, it provides APIs and services for application communication, including TN3270, FTP, Telnet and Enterprise Extender.
The product has built-in network management and monitoring support including tools for configuration, performance monitoring and problem diagnosis like Netstat, Packet Trace and Syslogd. It has full support for IPv6, helping to ensure future-proof networking capabilities.
What Are Its Components and What Do They Do?
This question is easily explained in the figure below. Six components cover access methods, services and facilities.
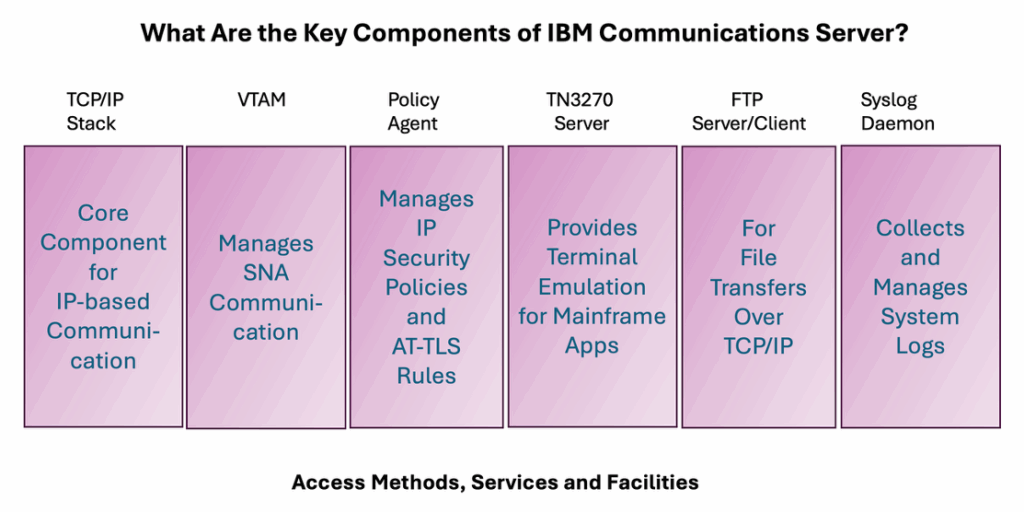
Figure 1. Components are a way to explain the IBM Communications Server product.
Does It Support Integration With Other z/OS Services?
IBM Communications Server is deeply integrated with other z/OS services as shown in the table below:
Table 2. IBM Communications Server and Integration With Other Products and Services
| Product or Tool | How Used |
| z/OSMF | For configuration and management via a web interface |
| RACF | For security and access control |
| Sysplex | For high availability and workload balancing |
| Workload Manager (WLM) | For performance optimization |
| System Management Facility (SMF) | For logging and auditing |
Let’s move on to another communications product that is important in z/OS.
What Is z/OS Enterprise Extender (EE)?
z/OS Enterprise Extender (EE) is a key component of IBM Communications Server for z/OS that enables SNA applications to communicate over an IP network using High Performance Routing (HPR). It essentially allows traditional mainframe applications that rely on SNA to operate over modern TCP/IP infrastructure without requiring changes to the applications themselves.
What Does Enterprise Extender Do?
Enterprise Extender encapsulates SNA traffic within UDP/IP packets, allowing it to traverse IP networks while maintaining the reliability and session management features of SNA. This is particularly useful in environments transitioning from traditional SNA networks to IP-based networks.
Key Features of Enterprise Extender
The key features are shown in Figure 2, below.
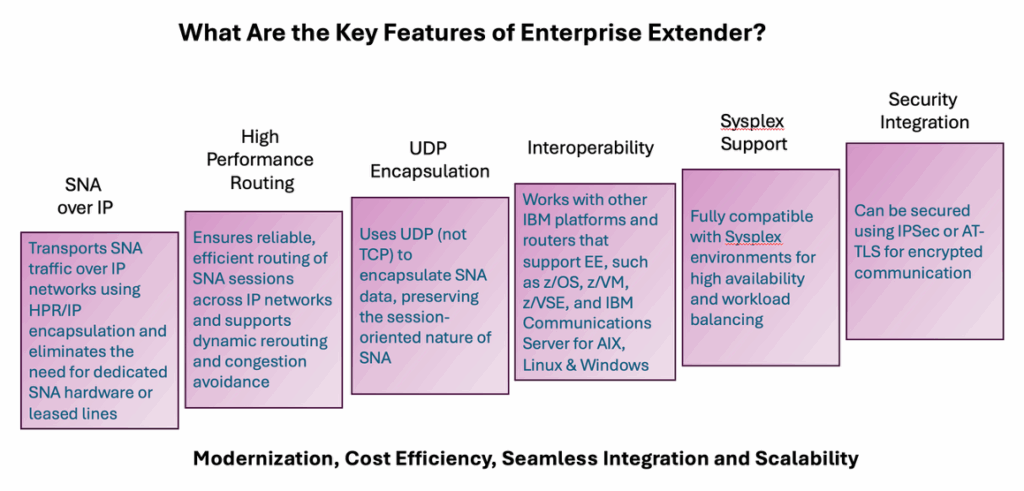
Figure 2. Six key features of EE.
Why Use Enterprise Extender?
Supporting modernization, EE allows legacy SNA applications to run over modern IP networks. Cost efficiency results from reducing the need for maintaining separate SNA infrastructure. Seamless Integration is possible with no changes required to existing SNA applications. Scalability is achieved by leveraging IP network scalability and routing capabilities.
Let’s move on to a third communications product that is important in z/OS.
What Is Sysplex Distributor?
Sysplex Distributor is a feature of IBM z/OS Communications Server that provides intelligent workload balancing for TCP/IP connections across multiple systems in a Parallel Sysplex environment. It enables high availability and scalability for TCP/IP-based applications by distributing incoming client requests to the most appropriate server instance within the Sysplex.
How Sysplex Distributor Works
Clients connect to a single Virtual IP Address (VIPA) that represents a service, not a specific system. This VIPA is shared across multiple z/OS systems in the Sysplex. Sysplex Distributor receives the incoming connection and uses Workload Manager (WLM) policies to determine the best target system. It then redirects or hands off the connection to the selected system. Dynamic VIPA (DVIPA) enables automatic reassignment of IP addresses in case of system failure, ensuring continuous availability.
Key Features of Sysplex Distributor
Five key features are summarized in the table below:
Table 3. Workload Balancing, High Availability, Scalability, Application Transparency and Security Integration with Sysplex Distributor
| Workload Balancing: Uses WLM policies to route traffic based on system load, availability and performance goals |
| High Availability: Supports failover and recovery by dynamically reassigning VIPAs to healthy systems |
| Scalability: Allows horizontal scaling of TCP/IP applications across multiple Logical Partitions (LPARs) |
| Application Transparency: Applications do not need to be aware of the distribution as they simply bind to a VIPA |
| Security Integration: Works with AT-TLS, IPSec and RACF for secure communication and access control |
Let’s move on to a fourth communications product that is important in z/OS.
What are HiperSockets?
HiperSockets is an advanced IBM z/Architecture feature that provides high-speed, memory-to-memory TCP/IP communication between LPARs on the same physical IBM Z server. It does this without using any physical network hardware.
What Makes HiperSockets Special?
Communication happens entirely in memory, bypassing traditional network interfaces like OSA cards. No physical network is required. The implementation supports ultra-low latency since data never leaves the system. Transmission is extremely fast and efficient. HiperSockets provides high throughput, making it ideal for high-volume, low-latency workloads such as database access, transaction processing and inter-application messaging.
Key Features of HiperSockets
Consider these five features as a brief recap:
- In-memory communication uses system memory as the transport medium between LPARs.
- The TCP/IP protocol is fully supported in a standard way so applications don’t need to change.
- Secured using z/OS features like IP filtering, AT-TLS and RACF so security support is robust.
- There are no external network dependencies, reducing points of failure, so reliability is ensured.
- Works seamlessly with z/OS Communications Server and other IBM Z networking features so integration is strong.
Typical Ways HiperSockets are Used
Candidates for employing HiperSockets functionality include communication between CICS regions in different LPARs, Db2 subsystems and application servers and WebSphere Application Server instances. Another candidate is high-speed data exchange in Parallel Sysplex environments.
The benefits are significant. HiperSockets reduces network complexity and hardware costs, improves performance and reliability and enhances security by keeping traffic within the system.
What About Security Integration in z/OS Networking?
Security is effective in z/OS Networking. Security works with z/OS networking because of integration with RACF as it controls access to network resources. Also, integration with the Application Transparent Transport Layer (IPSec and AT-TLS) ensures secure communication and firewall support. Additionally, Intrusion Detection Services (IDS) are built into z/OS Communications Server. Encryption and compliance are also part of IBM z/OS Communications Server as it includes capabilities like TLS, IPsec and SSH for secure data transmission. All these components work together to make networking security effective.
Best Practices and Performance Tuning
Here is a summary of powerful suggestions. The first group contains suggested best practices in five areas. Please note, several of the items have links regarding additional items to consider.
z/OS Networking Best Practices
1. Use Sysplex networking features. Sysplex Distributor load balances TCP/IP workloads across LPARs. Dynamic VIPA (DVIPA) is important as it enables IP mobility and high availability. Consider XCF-over-HiperSockets as it reduces latency for intra-CPC communication.
2. Optimize TCP/IP Stack Configuration. Tune TCP/IP profile parameters like TCPCONFIG, DEVICE, BEGINROUTES and AUTOLOG. Use IPCONFIG and VIPADYNAMIC for flexible IP management. Enable IPv6 where applicable for futureproofing.
3. Implement Policy-Based Routing. Use Policy Agent (PAGENT) to manage IPsec, QoS and routing policies. Apply QoS policies to prioritize critical workloads.
4. Secure Network Traffic. Use IPSec for encrypted communication. Enable AT-TLS (Application Transparent TLS) for secure sockets. Monitor with z/OS Encryption Readiness Technology (zERT) to ensure compliance.
5. Leverage HiperSockets and RoCE. Exploit memory-to-memory TCP/IP communication within Central Processor Complex (CPC). RDMA over Converged Ethernet (RoCE) provides high-speed, low-latency networking between CPCs.
z/OS Networking Performance Tuning Techniques
This second group contains performance tuning suggestions in five areas.
1. Monitor with SMF and RMF. Use SMF 119 records for TCP/IP stack performance. Analyze RMF Network Activity Reports for throughput, latency and errors.
2. Tune Buffer Sizes and MTU. Adjust TCP window sizes, MTU and buffer pools for optimal throughput. Use NETSTAT and IPTRACE to diagnose bottlenecks.
3. Optimize Workload Manager (WLM) Policies. Ensure networking tasks are properly classified and prioritized. Use WLM goals to manage response times for network-heavy applications.
4. Use OMEGAMON and Other Tools. IBM OMEGAMON for Networks: Real-time monitoring and alerting.
5. Apply Latest APARs and PTFs. Regularly update with IBM-recommended fixes to improve stack performance and stability. Monitor IBM Techdocs and Tuning Letters for new tuning recommendations.
Figure 3, below, summarizes the best practices and tuning suggestions discussed in this section.
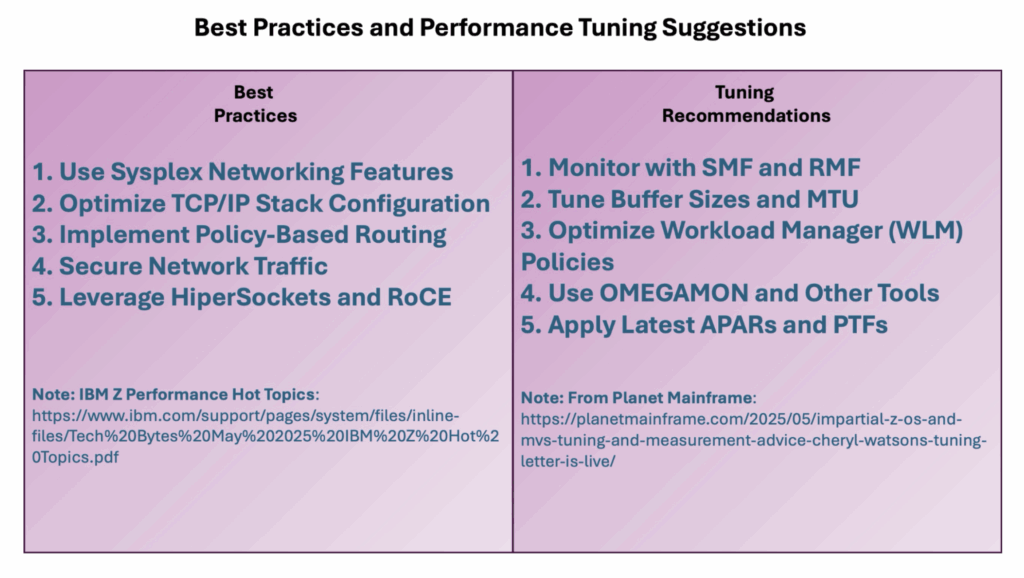
There Is Much to Discuss About z/OS Networking
In this article, I covered many dimensions of networking on z/OS. I have surveyed core network and application protocols and networking products that “mean business,” including IBM Communications Server, z/OS Enterprise Extender, Sysplex Distributor and HiperSockets. I have also explored networking integration around security and a brief discussion on best practices and performance tuning.
What’s Next?
The next article on networking will focus on the networking management and monitoring tools and products for z/OS. Also, I will explore integration, modernization and future trends.